Part 2: Setting up a Linux (Ubuntu) server.
This section explains how to set up a Linux server which is an incredibly useful thing to do. It is relatively easy and results in a powerful tool for doing all sorts of networking tasks as it is left on all the time. I highly recommend doing this (in fact, the all of this documentation assumes that you have a Linux server). I am using Ubuntu. You can use another Linux distribution if you want to.
Your server does not need to be very expensive — get an obsolete desktop from a friend who has upgraded. You can just use a 500 MHz machine with 512 MB RAM and a 10 GB hard drive. If you are planning on storing lots of files, get a 100GB hard drive or more.
You need to
(a) install Ubuntu,
(b) configure access control lists
(c) install and configure Open-SSH
(d) install and configure SAMBA,
(e) install and configure SQUID,
(f) probably install LSHELL
(g) set up port forwarding on your router
(a) Installing Ubuntu
- This is explained in many other places on the internet. I won't go over it here. It is not hard to do at all.
- I would recommend installing a long-term-support (LTS) Server version e.g. 10.04 LTS which is supported 'til 2015.
- Note that you will need to use a fixed IP address (e.g. 192.168.1.33) for port forwarding and everything else to work.
| Post install steps: |
| sudo apt-get update && sudo apt-get upgrade |
| If you can't access the internet then modify these files (to get DNS to work) |
| sudo vi /etc/network/interfaces sudo vi /etc/resolv.conf #restart networking sudo /etc/init.d/networking restart |
(b) Configuring ACL (access control lists).
There is some overlap between ACLs and the options in sshd_config. Access Control Lists are essentially a firewall, but easier to use than "iptables". Use ACLs if you want to restrict access to your computer to only a few source IPs. Normally this is not that useful as I may be at a hotel or a friend's house and want to connect to my home server. This is only really applicable if you are able to login (using SSH) to another external computer on the internet - you can use this to improve the security of your home server. If you do have this ability then see section 5 on how to configure ACLs.
(c) Set up SSH server on Fishbuntu
Again, this is very easy. Just install the server, change the config file (for sshd not ssh) and then restart sshd
For security you must change the port number. The default is port 22, which is regularly attacked by hackers. Make it a number greater than 1024 that is not used for some other service, typically somewhere in the 2000 range. For this document I am using 2202. You must use the same port number when you set up port forwarding on your router.
| Install SSHD-server. This will setup server keys. It is recommended to reboot after installing OpenSSH-server. |
| sudo apt-get install openssh-server #reboot sudo shutdown -r now |
| Edit sshd_conf |
| sudo vi /etc/ssh/sshd_config <...> # What ports, IPs and protocols we listen for #Port 22 Port 2202 # Change to no to disable tunnelled clear text passwords # set to NO **only** when you have public key access set up #PasswordAuthentication yes PasswordAuthentication no #PermitRootLogin yes PermitRootLogin no #only allow specific users to use SSH AllowUsers rubio gia123 |
| You must restart the ssh daemon for any config changes take effect |
| sudo /etc/init.d/ssh restart |
Once PrivateKey Authentication is working (see next page), disable password access by adding "PasswordAuthentication no" as seen above.
(d) Install and configure SAMBA
Samba is a file server program that allows Windows machines to access files on Linux machines.
- This is described elsewhere and is not really part of using SSH. It
is mostly for local networks that don't use SSH.
I believe that if your laptop is using Ubuntu, then you can access Samba shares through SSH, but I haven't got it working yet.
(e) Install and configure SQUID
Squid is a proxy server that does a bunch of useful things.
| Installing SQUID: |
| sudo apt-get install squid #install modules for Webmin - squid logs and squid cache manager sudo apt-get install sarg squid-cgi |
| Configure Squid: Since you will be routing it through SSH, you don't need to configure much (no auth_param, ACL lists, ncsa_auth, ...) The main thing is not to open up port 3128 on your router. |
| sudo vi /etc/squid/squid.conf # We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only # one who can access services on "localhost" is a local user # Uncomment this. I don't remember why. http_access deny to_localhost #put your hostname here visible_hostname aaa.bbb.com #Just leave the port the same. Only use port 3128. Port 443 needs squid to be compiled with a --SSL option http_port 3128 #https_port 443 sudo /etc/init.d/squid reload |
(f) Install LSHELL
Lshell is a Limited Shell, written in Python. It is used when you need to allow someone else access to your system and you want to limit what they are allowed to do. I use it for two things: (i) for the reverse SSH connection from the WorkLinSrv computer (so that if someone at work uses that computer, they can't access everything on my home computer), (ii) if I wanted to allow a colleague to print from home, I would set it up so that he logs in to this account. [The version described below is not the latest. Use the most recent version.]
| Installing LSHELL: Download the software, and complile it, then make the directory /var/log/lshell |
| wget http://downloads.sourceforge.net/project/lshell/lshell/0.9.7/lshell-0.9.7.tar.gz?use_mirror=voxel #or dpkg -i lshell_0.9.3-2_i386.deb ?? gunzip lshell* tar -xvf lshell* cd lshell-0.9.7 sudo python setup.py install sudo mkdir /var/log/lshell sudo chmod 700 /var/log/lshell |
| Edit /etc/lshell.conf and make the changes in the sections indicated below |
| sudo vi /etc/lshell.conf [default] ## a list of the allowed commands or 'all' to allow all commands in user's PATH #allowed : ['ls','echo','cd','ll'] allowed : ['ls','uname'] ## command aliases list (similar to bash's alias directive) # comment out aliases #aliases : {'ll':'ls -l', 'vi':'vim'} ## logging strictness. If set to 1, any unknown command is considered as ## forbidden, and user's warning counter is decreased. If set to 0, command is ## considered as unknown, and user is only warned (i.e. *** unknown synthax) # enable this. strict : 1 |
| Type in these commands to create the user gia321 (who will be a limited shell user) |
| sudo adduser gia321 # add user, prompted for all information sudo adduser gia321 users # add to users group (this may not always be desirable) #Type in these commands to create the group lshellg and add user gia321 to it: sudo groupadd lshellg sudo chown :lshellg /var/log/lshell sudo usermod -aG lshellg gia321 #change the login shell for user gia321 in /etc/passwd: sudo chsh -s /usr/bin/lshell gia321 |
(g) Set up port forwarding on your router.
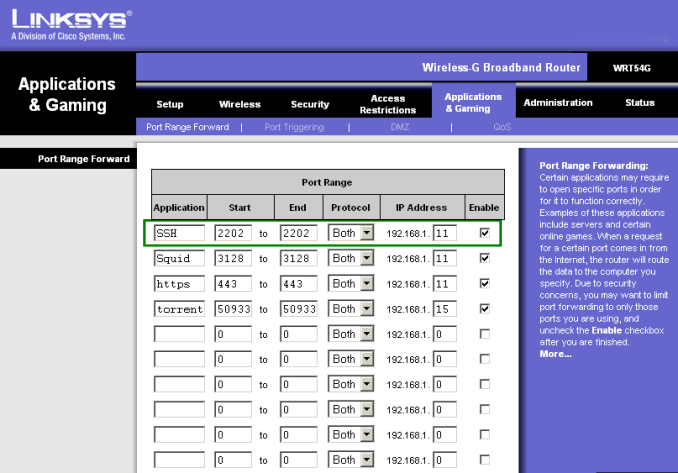
- For security reasons, you only want a few ports on your home network that are open to the internet. These are ports that are always open, that can be accessed from the internet side. (Any number of ports can be opened from the local computer side, for example, when you run Firefox, it will open port 80 and browse the web through that.)
- Notice that all of the open ports go to our linux server, Fishbuntu (192.168.1.11). Linux is a lot easier to secure that than Windows computers are.
- The only exception is a torrent port which goes to a special partition on one of my computers which is not visible to any other operating system. If something gets trashed via torrent, then no harm done to the rest of my network, I just delete that partition and reinstall it from a pristine backup partition. (This is done using the program BootitNG. It is an amazingly powerful boot manager and partition manager. I won't describe how I use it here, since it's off topic.)
- Setting your SSH port to anything other than 22 is an essential security feature. For this document, I have set it to 2202. This significantly reduces the chances of hackers breaking in. Be aware though, that this is to some extent "security through obscurity" which is an oxymoron.
- Using SSH completely (as things are described in this document) means that I should actually disable the two SQUID ports (3128 and 443). I initially enabled them because I wanted to do a quick bypass of the webproxy at work and didn't want to bother encrypting what my browser is doing. Do not do this. Close everything except the SSH port.
- What this port forwarding is doing, is saying that nothing can access anything on my local home network unless it goes through my SSH (port 2202) to my Linux server. Everything must go through this server before going to anything else in my home network.
- Problem: A bug has been reported in the some protocol somewhere (see reddit article). From a remote location, only the HTTP and HTTPS requests go through the encrypted tunnel. The DNS requests don't. This means that sniffers can see what your DNS requests are. Solution: use a SOCKS5 proxy connection.
